Question
Time left
Score
0
What is the answer to this questions?
A
Choice 1
B
Choice 2
C
Choice 3
D
Choice 4
Below are the skills measured in this category:
1
Describe general security and network security features (10-15%)
Describe Azure security features
Describe basic features of Azure Security Center, including policy compliance, security
alerts, secure score, and resource hygiene
Describe the functionality and usage of Key Vault
Describe the functionality and usage of Azure Sentinel
Describe the functionality and usage of Azure Dedicated Hosts
2
Describe Azure network security
describe the concept of defense in depth
describe the functionality and usage of Network Security Groups (NSG)
describe the functionality and usage of Azure Firewall
describe the functionality and usage of Azure DDoS protection
3
Describe identity, governance, privacy, and compliance features (20-
25%)
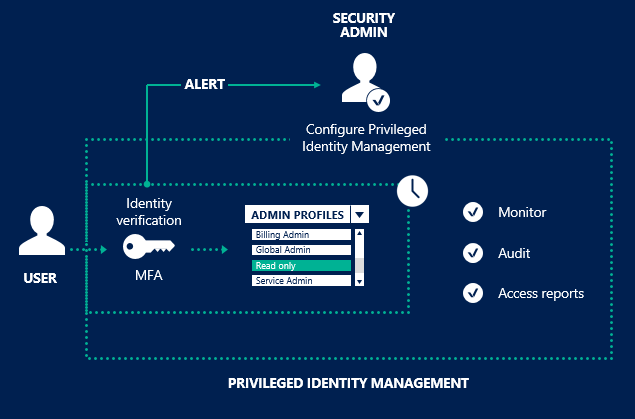
Describe core Azure identity services
explain the difference between authentication and authorization
define Azure Active Directory
describe the functionality and usage of Azure Active Directory
describe the functionality and usage of Conditional Access, Multi-Factor Authentication
(MFA), and Single Sign-On (SSO)
4
Describe Azure governance features
Describe the functionality and usage of Role-Based Access Control (RBAC)
Describe the functionality and usage of resource locks
Describe the functionality and usage of tags
Describe the functionality and usage of Azure Policy
Describe the functionality and usage of Azure Blueprints
Describe the Cloud Adoption Framework for Azure
5
Describe privacy and compliance resources
Describe the Microsoft core tenets of Security, Privacy, and Compliance
Describe the purpose of the Microsoft Privacy Statement, Online Services Terms (OST)
and Data Protection Amendment (DPA)
Describe the purpose of the Trust Center
Describe the purpose of the Azure compliance documentation
Describe the purpose of Azure Sovereign Regions (Azure Government cloud services and
Azure China cloud services)
Having a good security strategy is essential in today's digital world. Every application and service, whether on-premises or in the cloud, needs to be designed with security in mind. Security needs to happen at the application level, at the data level, and at the network level.
Learn about the various Azure services you can use to help ensure that your cloud resources are safe, secure, and trusted.
Below are some common Azure Security and Privacy Services
0
Azure DDoS Protection
Protects Azure-hosted applications from distributed denial of service (DDOS) attacks.
1
Azure ExpressRoute
Connects to Azure over high-bandwidth dedicated secure connections.
2
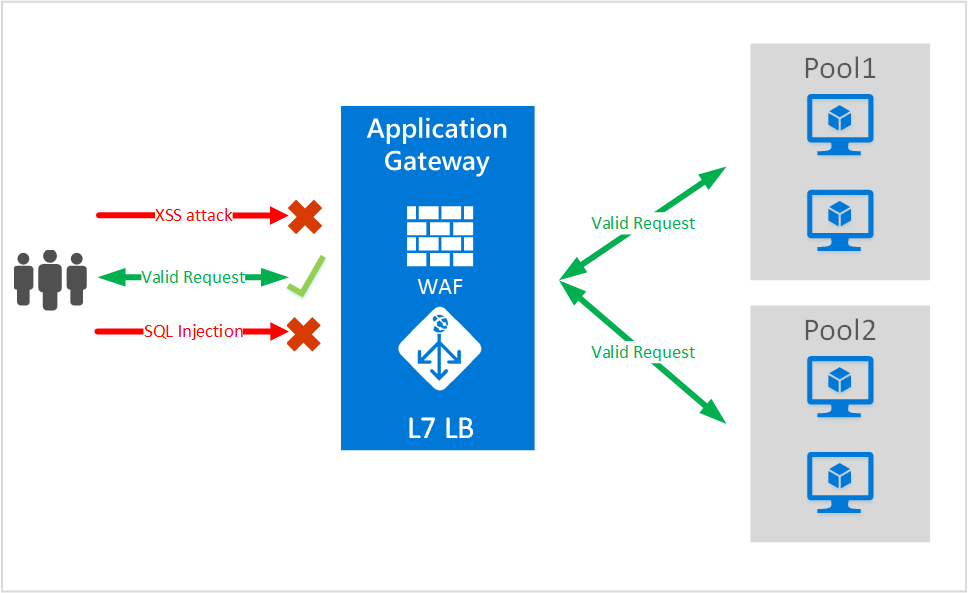
Azure Firewall
Implements high-security, high-availability firewall with unlimited scalability.
3
Azure Key Vault
Azure Key Vault is a centralized cloud service for storing an application's secrets in a single, central location. It provides secure access to sensitive information by providing access control and logging capabilities.
Azure Key Vault can help you: Manage secrets, Manage encryption keys, Manage SSL/TLS certificates, Store secrets backed by hardware security modules (HSMs) etc..
The benefits of using Key Vault include:
- Centralized application secrets
- Securely stored secrets and keys
- Access monitoring and access control
- Simplified administration of application secrets
- Integration with other Azure services
4
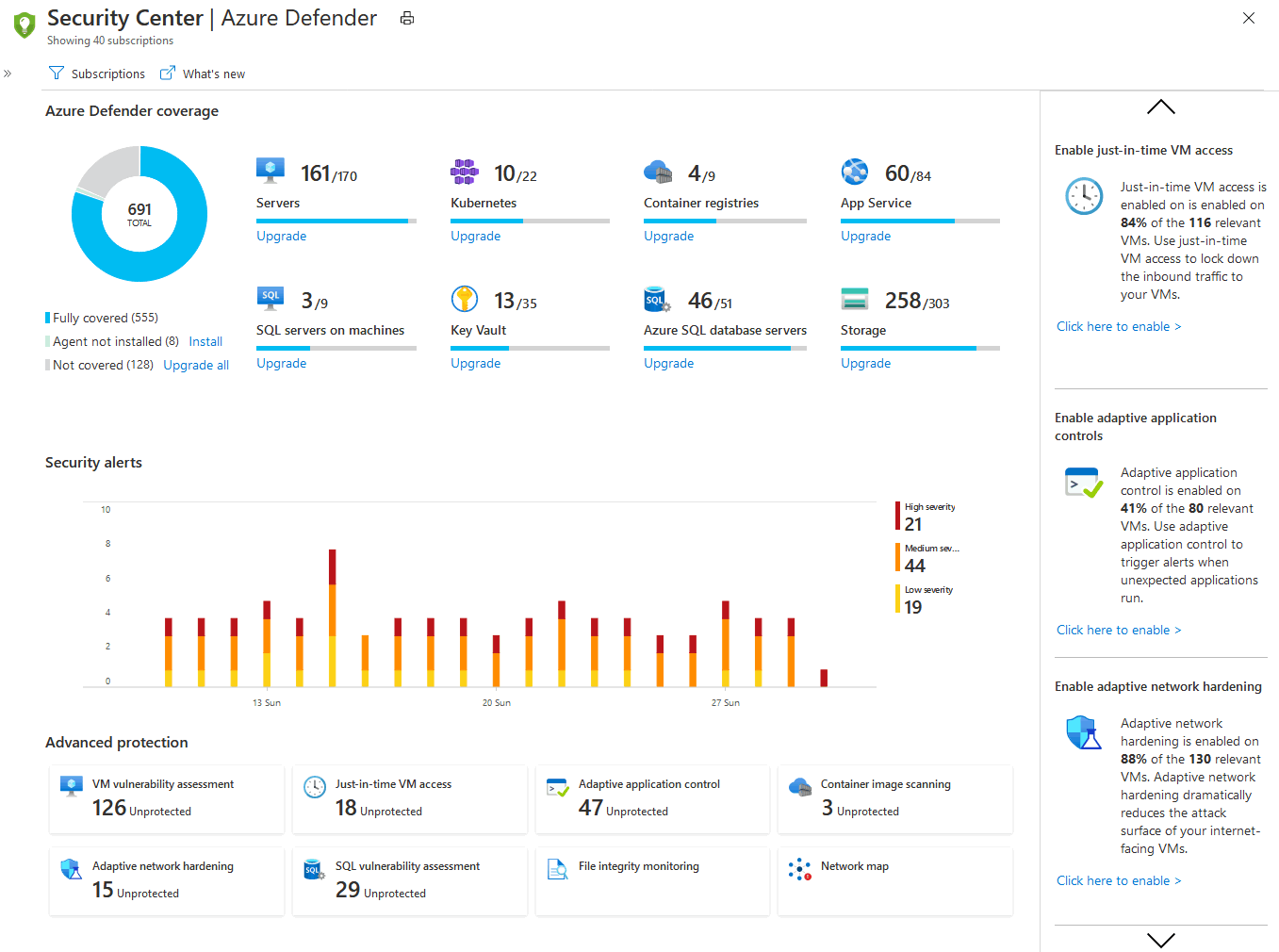
What's Azure Security Center?
Azure Security Center is a monitoring service that provides visibility of your security posture across all of your services, both on Azure and on-premises. The term security posture refers to cybersecurity policies and controls, as well as how well you can predict, prevent, and respond to security threats.
Security Center can:
- Monitor security settings across on-premises and cloud workloads.
- Automatically apply required security settings to new resources as they come online.
- Provide security recommendations that are based on your current configurations, resources, and networks.
- Continuously monitor your resources and perform automatic security assessments to identify potential vulnerabilities before those vulnerabilities can be exploited.
- Use machine learning to detect and block malware from being installed on your virtual machines (VMs) and other resources. You can also use adaptive application controls to define rules that list allowed applications to ensure that only applications you allow can run.
- Detect and analyze potential inbound attacks and investigate threats and any post-breach activity that might have occurred.
- Provide just-in-time access control for network ports. Doing so reduces your attack surface by ensuring that the network only allows traffic that you require at the time that you need it to.
5
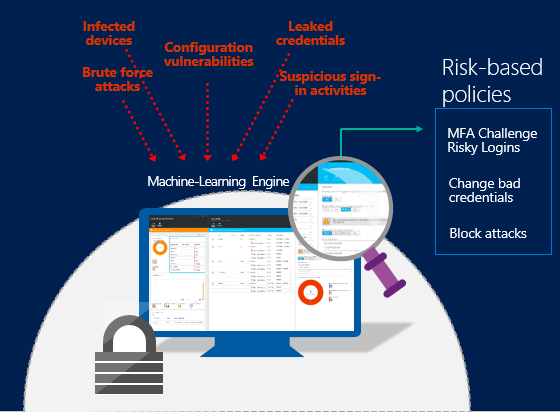
What's Azure Security Score?
Secure score is a measurement of an organization's security posture.
Secure score is based on security controls, or groups of related security recommendations. Your score is based on the percentage of security controls that you satisfy. The more security controls you satisfy, the higher the score you receive. Your score improves when you remediate all of the recommendations for a single resource within a control.
Secure score helps you:
- Report on the current state of your organization's security posture.
- Improve your security posture by providing discoverability, visibility, guidance, and control.
- Compare with benchmarks and establish key performance indicators (KPIs).
6
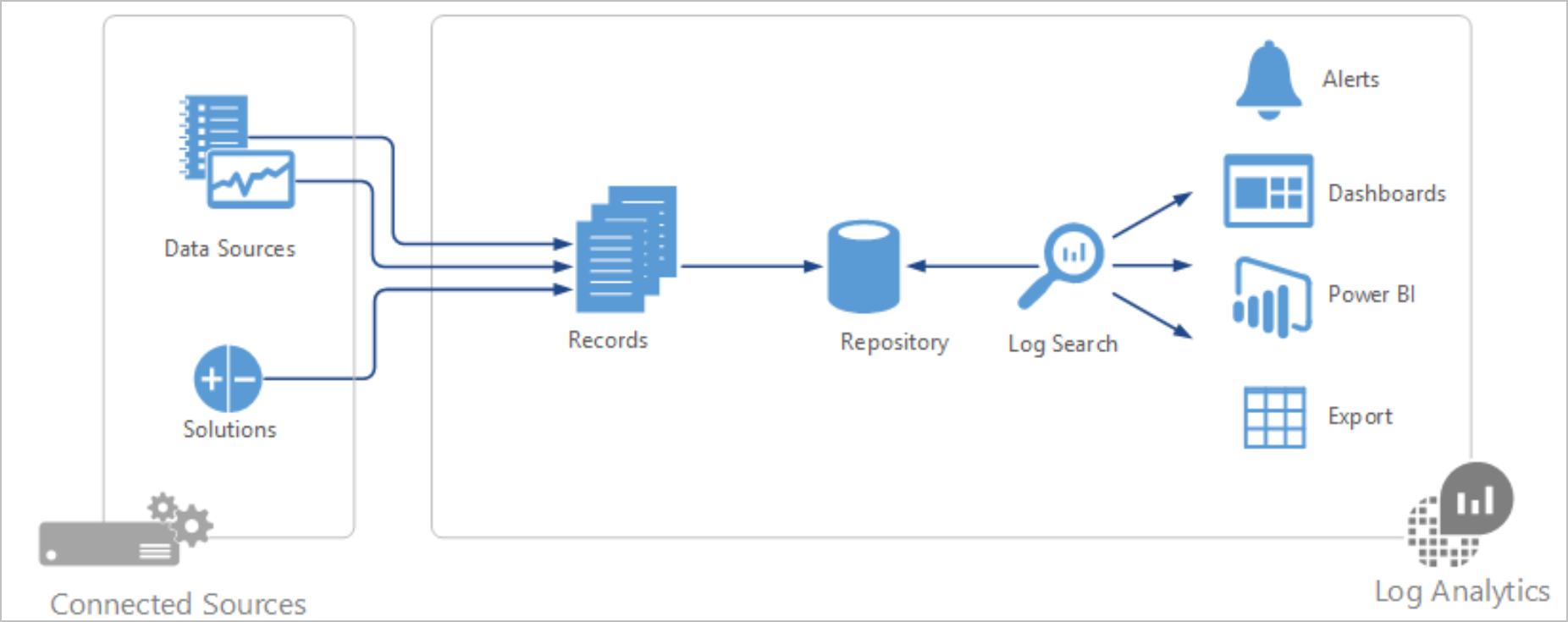
What's Azure Sentinel?
Azure Sentinel is Microsoft's cloud-based SIEM system. It uses intelligent security analytics and threat analysis.
Azure Sentinel enables you to:
- Collect cloud data at scale
Collect data across all users, devices, applications, and infrastructure, both on-premises and from multiple clouds.
- Detect previously undetected threats
- Minimize false positives by using Microsoft's comprehensive analytics and threat intelligence.
- Investigate threats with artificial intelligence
Examine suspicious activities at scale, tapping into years of cybersecurity experience from Microsoft.
- Respond to incidents rapidly
Utilize built-in orchestration and automation of common tasks.
6
What's the easiest way to combine security data from all of your monitoring tools into a single report that it can take action on?
- Collect security data in Azure Sentinel
- Azure Sentinel is Microsoft's cloud-based SIEM. A SIEM aggregates security data from many different sources to provide additional capabilities for threat detection and responding to threats.
7
How can a company enforce having only certain applications run on its VMs?
-
Create an application control rule in Azure Security Center
- With Azure Security Center, you can define a list of allowed applications to ensure that only applications you allow can run. Azure Security Center can also detect and block malware from being installed on your VMs.
8
Which is the best way for a company to safely store its certificates so that they're accessible to cloud VMs?
-
Store the certificates in Azure Key Vault
- Azure Key Vault enables you to store your secrets in a single, central location. Key Vault also makes it easier to enroll and renew certificates from public certificate authorities (CAs).
9
How can a company ensure that certain VM workloads are physically isolated from workloads being run by other Azure customers?
- Run the VMs on Azure Dedicated Host.
- Azure Dedicated Host provides dedicated physical servers to host your Azure VMs for Windows and Linux.